MacOS上的渗透测试工具 这些工具是运行在macOS 和 Linux上的. Enum4linux – depends on rpcclient, net, nmblookup, smbclient which are tools included with Samba and not found on macOS.
- Netdiscover Mac Os Versions
- Netdiscover Mac Os High Sierra
- Netdiscover Mac Os Mojave
- Mac Os Mojave
- Mac Os Catalina
- Netdiscover Mac Os High Sierra
- You can use netdiscoveron Mac OS, which is based on ARP packets. It will send ARP requests and scan the response. For example, run netdiscover command sudo netdiscover -i en0 -r 10.106.0.0/16in my local network would bring the following result.
- Nov 10, 2020 NetBrain Cloud-based paid service with a 14-day free trial, this network monitor includes autodiscovery features and some great mapping options. Intermapper Specialist network mapping tool for Windows, Linux, and Mac OS creates the layout of your current network after it searches via SNMP. The best network discovery tools and software.
Quite often, people will ask me where they should start in Hacking. Oh my gosh! There are soooo many topics, subjects, ideas, things to memorize, things to mess with, etc… It is much too difficult to tell someone where to start. Ummmm… I guess I might say you can start with reconnaissance. Or, if stuff in this article doesn't seem to make sense, you should probably start with a networking basics course. So, first you will want to find out about the other computers around you on a network. There are numerous ways to do this, but in this tutorial I will show you how to use a tool built into BackTrack / Kali that leverages Address Resolution Protocol or ARP to discover live hosts on the network.
As you know, ARP is used to map MAC addresses to IP addresses on an internal network. The router and switches send out broadcast ARP requests to all the MAC addresses on the network asking them to respond with their IP addresses. Each system will then respond with their IP address and the switch or other device will then create a small database that maps the MAC to the IP address, so that it it knows 'who is who'.
We can use this same protocol to discover the IP addresses on a corporate, educational, wireless or other network by using Netdiscover. Its a simple tool that simply sends out ARP's—just like a switch or router would—asking for everyone's IP address on the network. In this way, we can gather the IP's we need and then to attack those machines with a MitM attack, Metasploit or other attack.
Before we get started, let's open Wireshark and look at some normal network traffic. As you can see in the screenshot below, once we open Wireshark and just wait a short while, I begin to send ARP requests. Packets 2113 and 2114 show an ARP exchange. If you look at 2113 and then scan across to the info section to the far right, you can see 'who has 192.168.1.1?'. In the following packet, we see the response '192.168.1.1 is at xx:xx:xx:xx:xx:xx'. That is normal ARP traffic.
We can now create a filter in Wireshark to just look for ARP tarffic by typing 'arp' in the filter window at the upper left. Now, all we see is ARP traffic as Wireshark has filtered out everything else.
Now that we see a bit of normal ARP traffic and how it works, let's fire up BackTrack and abuse the ARP protocol to learn the IP and MAC addresses of everyone on the network.
Step 1: Find Netdiscover

Netdiscover Mac Os Versions
We can find netdiscover by going to either Backtrack or Kali.
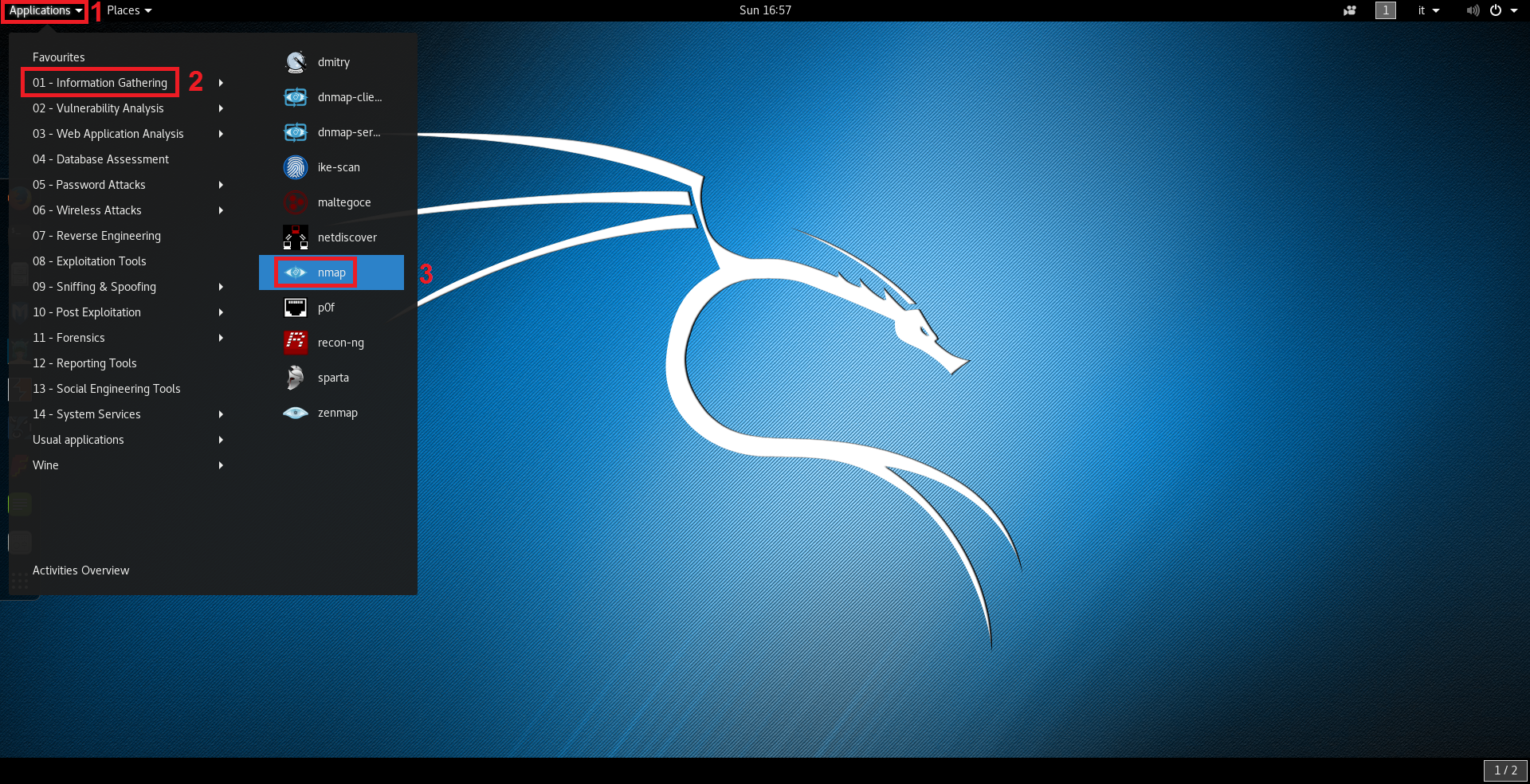
In Kali, go to the Kali Linux Menu –> Information Gathering –> Live Host Identification –>Netdiscover

In Backtrack, go to the Backtrack Menu –> Information Gathering –> Network Analysis –> Identify Live Hosts –> Netdiscover.
Step 2: Open Netdiscover
When we click on netdiscover, it opens a screen like that below and displays some basic help. Netdiscover is a relatively simple tool, so there are not a lot of options.
Step 3: Netdiscover Command
To discover the IP's on an internal network, we will usually want to scan a range of IP addresses. In netdiscover, we can use the -r switch (for range) and then in CIDR notation provide it the network range we want it to scan. In the command below, we are asking netdiscover to find all the live hosts with IP addresses between 192.168.1.1 to 192.168.1.255. We do this by typing;
Netdiscover Mac Os High Sierra
Netdiscover Mac Os Mojave
netdiscover -r 192.168.1.0/24
Mac Os Mojave

Netdiscover Mac Os Versions
We can find netdiscover by going to either Backtrack or Kali.
In Kali, go to the Kali Linux Menu –> Information Gathering –> Live Host Identification –>Netdiscover
In Backtrack, go to the Backtrack Menu –> Information Gathering –> Network Analysis –> Identify Live Hosts –> Netdiscover.
Step 2: Open Netdiscover
When we click on netdiscover, it opens a screen like that below and displays some basic help. Netdiscover is a relatively simple tool, so there are not a lot of options.
Step 3: Netdiscover Command
To discover the IP's on an internal network, we will usually want to scan a range of IP addresses. In netdiscover, we can use the -r switch (for range) and then in CIDR notation provide it the network range we want it to scan. In the command below, we are asking netdiscover to find all the live hosts with IP addresses between 192.168.1.1 to 192.168.1.255. We do this by typing;
Netdiscover Mac Os High Sierra
Netdiscover Mac Os Mojave
netdiscover -r 192.168.1.0/24
Mac Os Mojave
Step 4: Activate Netdiscover
Mac Os Catalina
As soon as we enter the command, netdiscover begins sending out ARP requests over the network and then logging the results on our screen. The process is live and interactive, so that as soon as new machines come on the network they pop up on our screen.
Netdiscover Mac Os High Sierra
Netdiscover is a simple but powerful tool that uses the ARP protocol to discover live network hosts. As long as you are connected to the network and ARP is enabled on the network, you should be able to discover every live host's IP and MAC address. Once you have those, then you can begin your strategy of exploiting those hosts.
